What is Personal Data?
In 2025, in the era of the data economy, personal data has become a key asset for businesses and organizations, creating various added values.
According to the Personal Information Protection Act, personal data refers to information about a living individual that can identify them. This includes not only basic personal details like name and resident registration number, but also a range of other data such as social and economic status, education, health/medical information, financial data, cultural activities, and even political opinions. In essence, personal data covers various types of information that reflect both the every aspect of an individual's life and their preferences.
The Importance of Personal Data Utilization and Security

Personal data is essential for efficient service delivery, personalized customer experiences, and data-driven decision-making, making it essential across industries and public sectors. It has become a key ingredient in areas such as administration, e-commerce, customer management, and financial transactions, playing a vital role in the structure, maintenance, and growth of society. The advancement of big data analytics has further accelerated the use of personal data.
For example, in public institutions, administrators can access citizen's personal data to aid processing, helping resolve issues more quickly. Similarly, businesses analyze consumer data to offer personalized services tailored to individual preferences. However, if personal data is stolen or leaked for malicious purposes, it can cause significant damage not only to individuals but also to organizations. Leaks can lead to account theft, spam emails, illegal telemarketing and other criminal activities.
Therefore, organizations dealing with sensitive personal data must prioritize data security. Both the systems handling personal data and the administrators with access to this data need to be secured. Public systems that process large volumes of sensitive data are especially focused on minimizing administrator access rights to prevent data breaches. Furthermore, they enhance protection by regularly checking access logs and implementing robust monitoring practices to safeguard personal data.
Current Issues with Personal Data Protection Measures
Personal data protection involves more than just encrypting and securely storing the data; it requires security at every stage of the data's lifecycle-from storing, sending and providing data. Despite ongoing efforts to secure personal data, several issues remain.
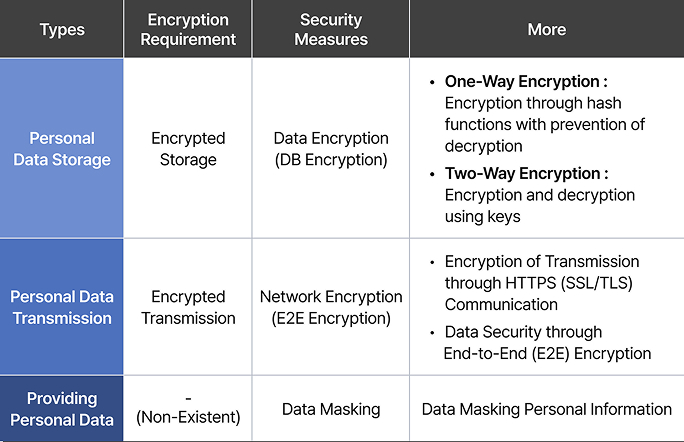
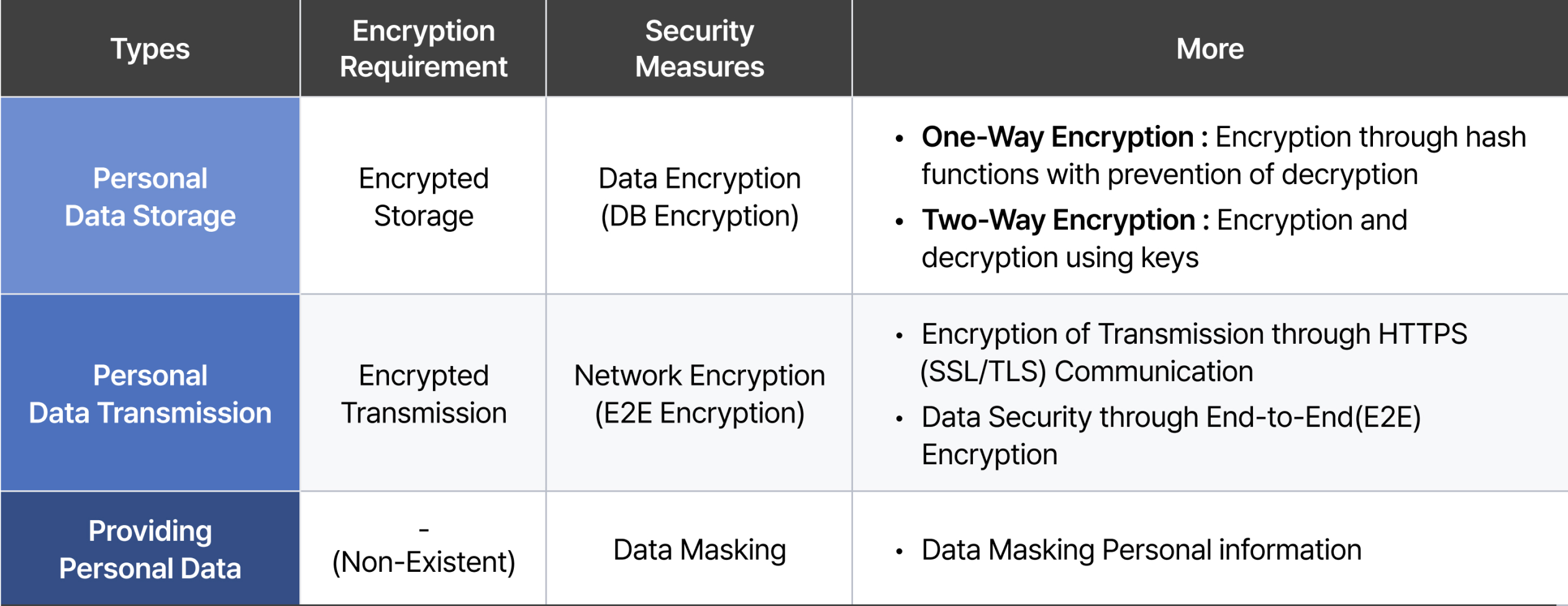
Currently, companies ensure the safe protection of personal data through data encryption in accordance with the Personal Information Protection Act when the data is stored in internal information processing systems. Additionally, when personal data is transmitted, network encryption is used to securely transfer the data.
However, the issue arises when the encrypted personal data reaches the web browser, where the original data is exposed in plaintext. To address this vulnerability, companies initially prevent data exposure by using data masking techniques such as asterisks(*), but in some cases, masked personal data may still expose important and sensitive information, such as personal ID or registration number, to be unmasked or reveal the data based on the user's role by providing an option to unmask it with ease.
Especially in boundaries like HR, where personal data needs to be readily accessed, the original data often has to be exposed for certain tasks. In such cases, personal information is inevitably provided in plaintext, and this data exists in the DOM area as plaintext. Additionally, frequently used personal data such as email addresses and phone numbers may also be provided in their original form, making them targets for scraping and crawling.
Even with strong encryption applied to databases to protect personal data, once the personal data is provided through the web, it is exposed, becoming a target for scraping and crawling attacks.
Limitations of Personal Data Encryption : 1. The Inevitability of Decryption
Personal data encryption is an essential security measure for data protection, but encryption alone cannot completely prevent personal data leakage. Encrypted personal data inevitably requires a decryption process, highlighting that encryption alone cannot ensure complete data security.
While encryption plays a key role in protecting data, in order for the data to be actively utilized, it must be decrypted on the web server. During this process, there is a high possibility of personal data being exposed or replicated. Therefore, personal data encryption primarily serves as a protection measure during the data storage and saving stages. Without strengthening security measures during the process of providing personal data, data encryption alone cannot prevent data leakage or breach issues.
Limitations of Personal Data Encryption : 2. Insider Threats
While organizations and companies implement various measures to prevent personal data leakage, a significant portion of data breaches comes from insiders. According to a statement from the Headquarters of the Korean National Police, most corporate data breaches are committed by internal parties. For example, a June 22, 2022 article in Security News revealed that a public servant from Gwonseon-gu, Suwon, abused their access rights to the Automobile Management Information System and Construction Machinery System for illegal street vendor enforcement and construction machinery operator license issuance. They unlawfully leaked 1,101 pieces of personal data to a private investigator.
This type of personal data leakage, where individuals with authorized access misuse their permissions to leak data, is an issue that arises at the decryption stage,representing a misuse of authority that encryption alone cannot solve. These cases highlight the vulnerability of personal data once decrypted and accessed by an authorized user.
So, to protect personal data, not only the data itself but also the individuals with access to that data must be securely managed. The solution to this lies in implementing strong access control policies, continuous monitoring, and strict auditing of individuals with access to sensitive data, ensuring that permissions are properly managed and misuse is detected early. This will help prevent unauthorized actions and limit the risk of insider threats.
Personal Data Protection through Data Obfuscation


Again, to ensure the secure protection of personal data, encryption alone is never sufficient. Continuous protection through data obfuscation is necessary. In environments where large amounts of personal data are requested and utilized, companies and organizations must go beyond simply storing data securely. It is essential to protect sensitive data continuously through obfuscation during the process of using personal data.
Additionally, even administrators, who have access to personal data, must be provided with the data heavily obfuscated to prevent abuse of authority or unintentional leaks. This ensures that even if personal data is leaked, when personal data remains obfuscated and unreadable, thus preventing misuse.
Web-based corporate systems, in particular, have vulnerabilities because they allow easy extraction of original data using web scraping tools or basic web browser functions. Therefore, in addition to preventing scraping and crawling, it is crucial to control browser functions to protect personal data from leakage. By implementing such measures, organizations can provide an added layer of security for personal data, ensuring it is protected from unauthorized access and exploitation.
Real-Time Personal Data Obfuscation
Once encrypted personal data reaches the web browser, the original data containing personal information must remain obfuscated. Through data obfuscation, the extraction of personal data becomes impossible and the personal information displayed on the screen is dynamically obfuscated in the DOM, preventing analysis and interpretation of the data.
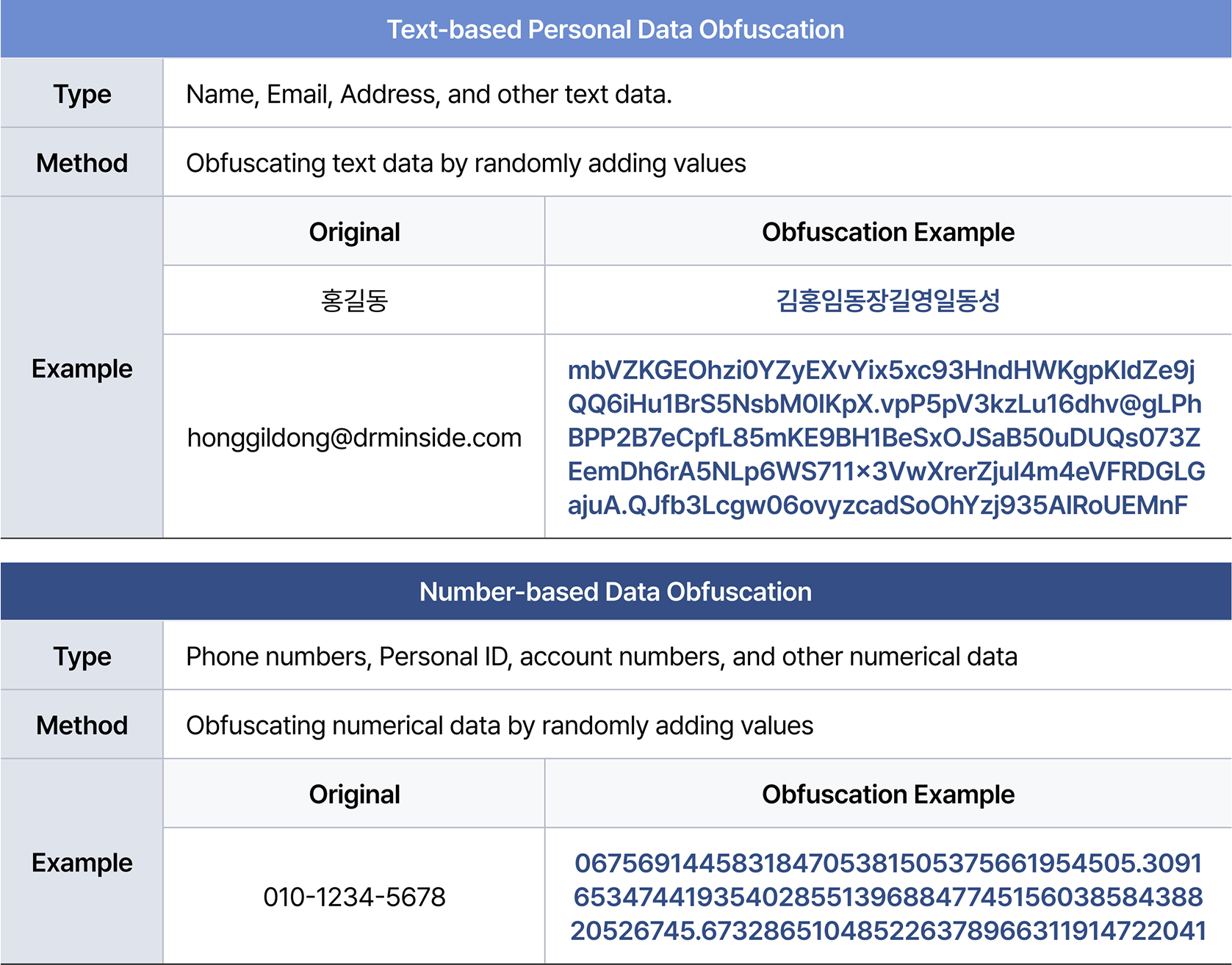
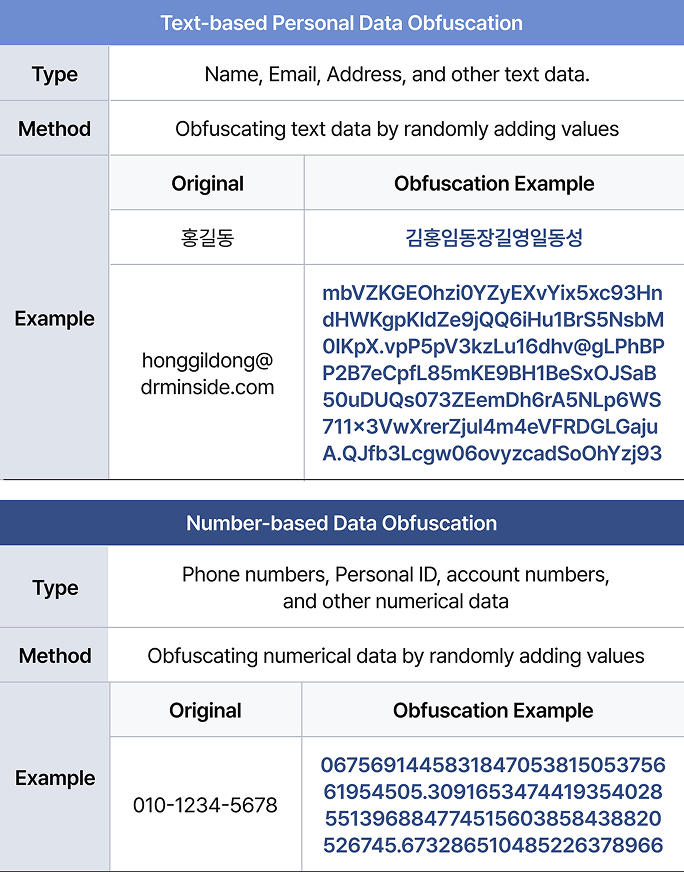
Data Obfuscation by Personal Data Type
Unlike regular text, personal data requires customized obfuscation techniques depending on its type. For example, numeric data such as phone numbers or personal ID numbers need a specific obfuscation approach, where garbage units based on numbers are added to ensure proper obfuscation. Each type of personal data should be handled with an appropriate obfuscation method to maintain security,ensuring that sensitive information is effectively protected from unauthorized access and misuse.
Building a Secure Digital Environment through Personal Data Obfuscation
As personal data becomes a core asset in the digital society, ensuring its secure protection has become a critical task for all organizations. Especially when considering the risks posed by insider threats and vulnerabilities in web-based systems, protecting personal data must be treated as a mandatory obligation, not a choice.
Personal data obfuscation is a powerful security method that can protect sensitive personal data in real time and effectively address security issues like web scraping and insider threats. By applying unique obfuscation techniques tailored to the specific types of personal data, organizations can block the possibility of data leaks and ensure the safety of the data. This enables institutions and businesses to build a trusted data management environment, securing both privacy and reliability in their operations.
References :
[1] Personal Information Portal, https://www.privacy.go.kr/front/contents/cntntsView.do?contsNo=34
[2] Won Byung-cheol, Security News, "Personal Information Commission Fines Suwon City for Leaking Personal Information to Detective Agencies," June 22, 2022, https://m.boannews.com/html/detail.html?idx=107704
[3] Kim Young-myung, Security News, "Over 6.15 Million Cases of Personal Data Breaches in Educational Institutions Over the Past Four Years... 520,000 Cases Reported Until August This Year," October 10, 2024, https://m.boannews.com/html/detail.html?idx=133447
[4] Park Eun-joo, Security News, "The Other Culprits Behind Personal Data Leaks: ‘Insiders’... The Criminal is Within," April 3, 2023, https://www.boannews.com/media/view.asp?idx=115440
[5] Kim Ki-bae, Electronic Times, "[Security Column] How Can We Prevent Endless Personal Data Breaches?" April 26, 2022, https://www.etnews.com/20220426000232